FWFG: pro and cons A-A vs A-P cluster firewall
26.03 2024 | by massimilianoLe seguenti tabelle indicano PRO e CONTRO di un modello cluster Firewall in Active-Active oppure in Active-Passive Mode Status PRO […]
Le seguenti tabelle indicano PRO e CONTRO di un modello cluster Firewall in Active-Active oppure in Active-Passive
| Mode | Status | PRO | CONS |
| A-P | active-passive | Creation VDOM partioning (vclustering); Right settings primary unit based on ASIS network architecture (the ASIS network architecture not provide ECMP between cluster firewall and switch/routers adjacents; Easy troubleshooting in case of fault/disservice because the traffic is processed only by primary unit; | With UTM (unified threat management such as antivirus, web filtering, antispam, app-control, etc..) the overall performance could be slow down if applied on every vlan passing from only primary unit The traffic passing only from one unit primary cluster and so, this is always under pression about performance network |
| A-A | active-active | Load-balancing traffic flow between all units cluster; consist of a primary unit that receives all data session and load balanced them among the primary unit with the secondary unit cluster; The secondary units are active only to process session content flows (in all other ways A-A work the same as A-P cluster); With UTM (unified threat management such as antivirus, web filtering, antispam, app-control, etc..) the overall performance could be better because shared between units cluster; Using FortiADC (Application Delivery Controller) to balance traffic flow in right and compatible ECMP mode between source and destination servers. | In case of issue it will be a mess to debug and analyze how it works (hard troubleshooting); Depends from network design (it is compatible with ECMP, but too much less when the network provide hsrp redundancy priority); Overall throughput bandwidth between MI3-MI5 for traffic to SYNC and monitor heartbeat among units cluster. |
| Mode | Status | Features |
| A-P | active-passive | Provides redundancy between the two nodes in hot-standby mode when the primary devices is affected by fault/disservice (failover protection). The cluster is build with one primary unit that processes traffic flow and syncrhonize all configuration with the second unit in standby status; the second unit do not process data but in case of failure of primary unit, take the role of primary and failover occurred. |
| A-A | active-active | Allows traffic to be balanced across the nodes on cluster and also performs failover; in this mode all vdom are in active-active status. Both units receive the traffic flow and load-balancing is useful amont to two members and depend by ECMP (equal cost multi-path over static or dynamic routing protocol) configuration on adjacent routers. By default, A-A mode load-balancing distributes proxy-based security profile processing to all cluster units, but it is memory-intensive, so FGCP (FortiGate Control Protocol) may result in higher throughput because is distributed among all units. To be enable data synchronization: Layer 4 connection: synchronize TCP connection state data Layer 4 session: synchonize the source IP address table for persistence to Servers backend Layer 7 session: synchonize the source IP address fot persistence to Servers backend |
Esempio di TCP Flow Traffic on A-A cluster firewall
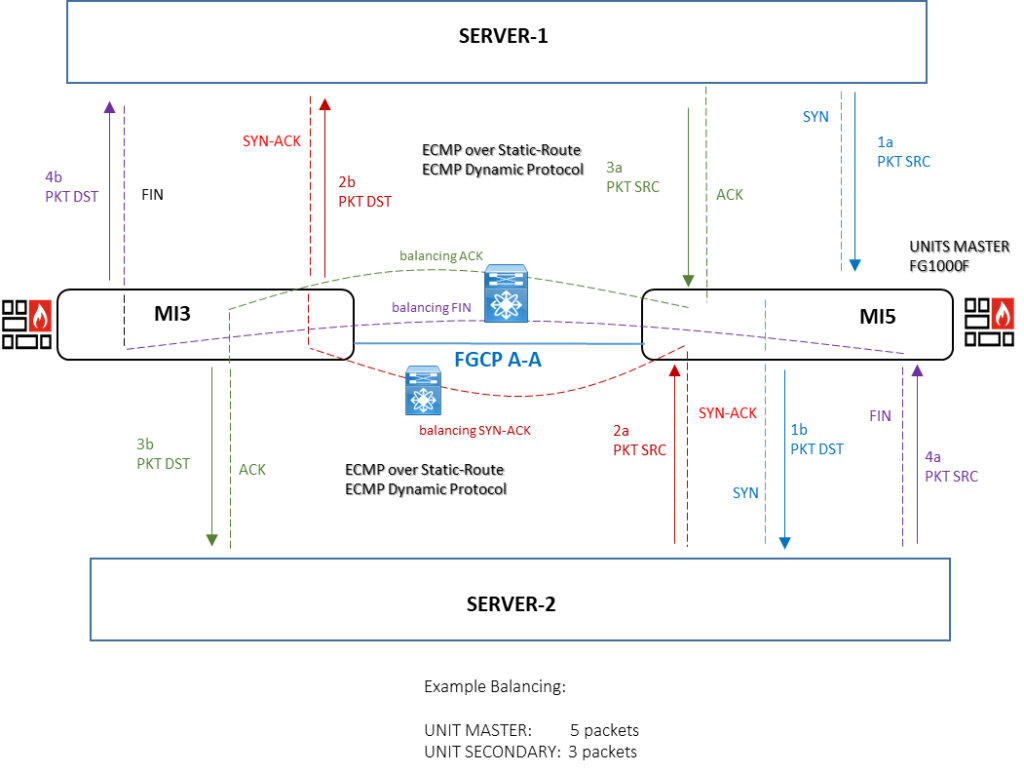
The A-A cluster Firewall balanced the traffic flow (session TCP):
The packet SRC is always direct to unit master associated with HA virtual MAC address and cluster IP address.
Then the unit master uses a load balancing schedule to distribuite session to the secondary units (including the primary); the secondary unit retain their MAC address and the master communicates with them using these MAC address.
Packet DST exiting the secondary unit proceed directly to their destination and do not pass through the master Unit.
By default A-A load balancing distributes proxy-based security profile processing to both cluster units.
Proxy-based security profile processing is CPU and memory-intensive.
The following proxy-based security profile processing is load balanced:
- Virus scanning
- Web filtering
- Email filtering
- Data leak prevention of HTTP, FTP, IMAP, IMAPS, POP3, POP3S, SMTP, SMTPS, IM, NNTP sessions
A-A does not load balance HTTPS session that have SSL deep packet scanning enable; this to prevent HTTPS web filtering problems.