802.1x: class-map and policy-map definitions (match, event, failure, action)
07.03 2024 | by massimilianoCLASS-MAP POLICY-MAP Esempio di configurazione 802.1x SWITCH Cisco aaa new-model!radius server <server_1>address ipv4 <ipv4_address_srv_1> auth-port 1812 acct-port 1813key 7 <shared […]
CLASS-MAP
POLICY-MAP
Esempio di configurazione 802.1x SWITCH Cisco
aaa new-model
!
radius server <server_1>
address ipv4 <ipv4_address_srv_1> auth-port 1812 acct-port 1813
key 7 <shared secret> # deve essere la stessa indicata in ISE
!
radius server <server_2>
address ipv4 <ipv4_address_srv_1> auth-port 1812 acct-port 1813
key 7 <shared secret> # deve essere la stessa indicata in ISE
!
aaa group server radius ISE-GROUP
server name <server_1>
server name <server_2>
ip radius source-interface Vlan5 #esempio vlan source
!
aaa authentication dot1x default group ISE-GROUP # network authentication
aaa authorization network default group ISE-GROUP # network access authorization
aaa accounting identity default start-stop group ISE-GROUP # send from switch accounting information to ISE at endpoint session start and end event
!
radius-server dead-criteria time 10 tries 3 # define how a switch mist detect a Radius server reachability failure; time = time during which no properly formed response received from ISE server; tries = the number of consecutive timeouts that must occur on the switch before the Radius server is marked dead
radius-server deadtime 15 # dead time is set to 15 minutes; With expiry of dead time, the switch will mark the server as alive again and begin sending RADIUS traffic to the server. If the RADIUS deadtime is not specified, it will default to a value of 0, which will bring the server back to the UP state right away.
Because of this behavior, the RADIUS server state could flap, causing additional authentication issues. To revert the server state back to the UP state before the specified deadtime expires, a RADIUS probe can be configured. This will periodically test the RADIUS server to see if it is responding to RADIUS requests. Upon receiving a response to a probe, the switch will mark the RADIUS server as alive.
Best-Ptactices Attribute for ISE
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
!
radius-server attribute 31 mac format ietf upper-case # non necessario
radius-server attribute 31 send nas-port-detail mac-only # include nas port e mac-address in calling-station-id (attribute 31) to access and accounting request (non necessario)
per passare da IBNS 1.0 to IBNS 2.0 eseguire il comando:
authentication display new-stile
URL redirection ACL
This ACL defines which traffic is redirected to ISE during the CWA, BYOD, and Posture scenarios. Any traffic that is permitted per ACL is redirected (192.168.1.10 in the example below). Implicit deny prevents other traffic types from being redirected. We recommend that you specify that only HTTP and HTTPS should be permitted since this traffic gets pushed to the switch CPU. If additional access control is needed in conjunction with the redirect ACL, we recommend that you use dACL in conjunction with the redirect ACL.
Note: ACL_WEBAUTH_REDIRECT or Pre-Auth-ACL are port-based ACL which are configured on the interface. However, the dACL or Per_User_ACL pushed from ISE takes precedence over the Port ACL that is applied to the Interface.
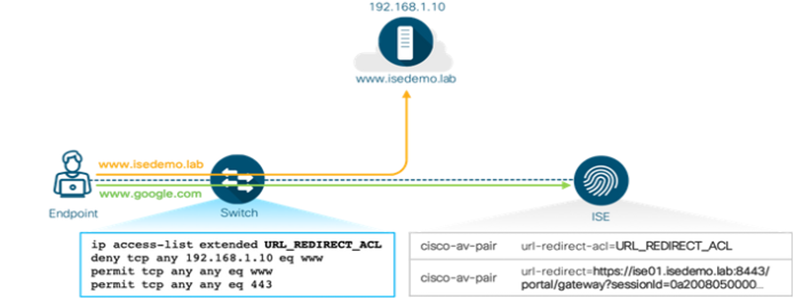
ip access-list extended IP-Adm-V4-Int-ACL-global
permit tcp any any eq www
permit tcp any any eq 443
Configure a Pre-Authentication ACL (Pre-Auth-ACL). This is required if the deployment transitions to low-impact mode
ip access-list extended preauth_v4
permit udp any eq bootpc any eq bootps
permit udp any any eq domain
deny ip any any
Global Basic Configuration
dot1x system-auth-control # enable 802.1x
access-session acl default passthrough # Optionally permette sessioni senza dACL (per-user Dynamic ACL) per connessioni to ACL-enabled interfaces con pieno accesso
Template USER-8021X (per IBNS 2.0)
template USERS-8021X
description users-8021x
switchport access vlan 157
switchport mode access
switchport voice vlan 100
access-session port-control auto
access-session host-mode multi-auth
authentication periodic # (Optional) Enable the reauthentication and inactivity timer for the port. Use the authentication periodic command to enable automatic reauthentication on a port whether the values are statically assigned on the port or are derived from the RADIUS server.
authentication timer reauthenticate server # (Optional) To specify the period of time to reauthenticate the authorized port and to allow the reauthentication timer interval (session timer) to be downloaded to the switch from the RADIUS server
mab
dot1x pae authenticator
dot1x timeout tx-period 10
trust device cisco-phone
service-policy type control subscriber PORT-AUTH-DOT1X
!
config Interfaces (IBNS 2.0)
interface range gi1/0/10-48
description PC+IPPHONE(8021X)
source template USERS-8021X
spanning-tree portfast
interface range gi1/0/1-5
description ACCESS-POINT(8021X)
source template USERS-8021X
spanning-tree portfast
spanning-tree bpdufilter enabled
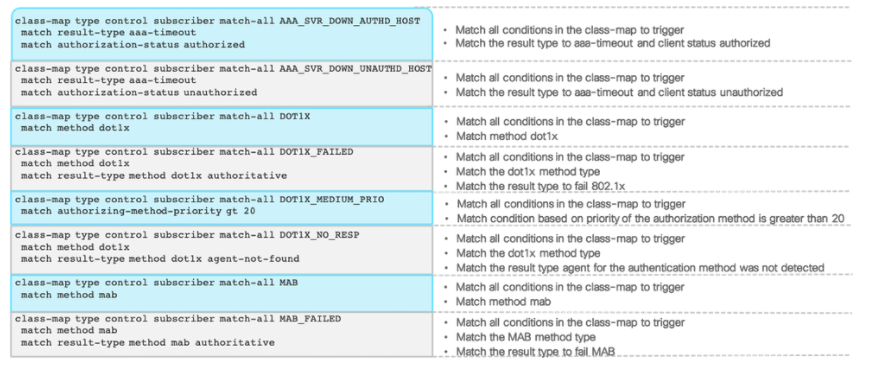
Class-Map
class-map type control subscriber match-all AAA_SVR_DOWN_AUTHD_HOST
match result-type aaa-timeout
match authorization-status authorized
!
class-map type control subscriber match-all AAA_SVR_DOWN_UNAUTHD_HOST
match result-type aaa-timeout
match authorization-status unauthorized
!
class-map type control subscriber match-all DOT1X_FAILED
match method dot1x
match result-type method dot1x authoritative
!
class-map type control subscriber match-all DOT1X_NO_RESP
match method dot1x
match result-type method dot1x agent-not-found
!
class-map type control subscriber match-all MAB_FAILED
match method mab
match result-type method mab authoritative
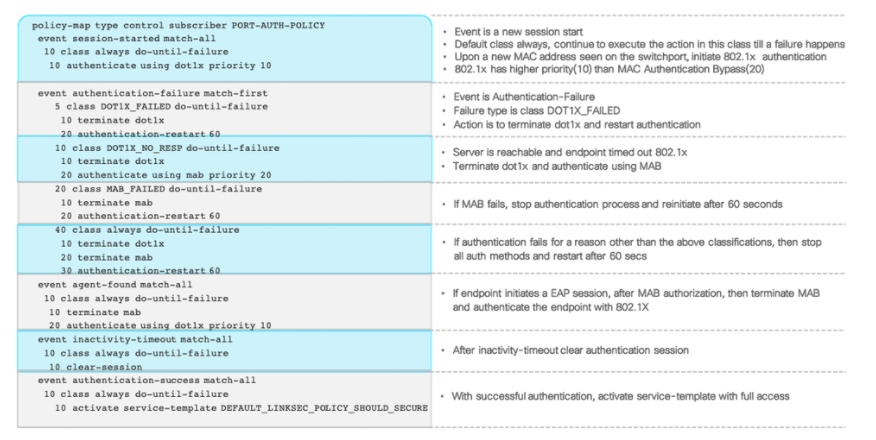
Policy-Map
policy-map type control subscriber PORT-AUTH-DOT1X
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x retries 2 retry-time 0 priority 10
event authentication-failure match-first
10 class AAA_SVR_DOWN_UNAUTHD_HOST do-until-failure
10 activate service-template USERS-8021X
20 authorize
20 class AAA_SVR_DOWN_AUTHD_HOST do-until-failure
10 activate service-template USERS-8021X
20 authorize
40 class DOT1X_NO_RESP do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
50 class MAB_FAILED do-until-failure
10 terminate mab
20 activate service-template USERS-8021X
30 authorize
60 class DOT1X_FAILED do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
70 class always do-until-failure
10 terminate dot1x
20 terminate mab
30 authentication-restart 60
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x retries 2 retry-time 0 priority 10
!
Nota:
Notice that the access-session closed command is part of the conversion and is being omitted in the interface template configuration. This is because the section focuses on low-impact mode, which is a minor variation of the open mode.
In IBNS 2.0, the default port mode is open mode. To move the port to closed mode, configure the access-session closed interface command explicitly either within the interface template or on the physical port.
Reset the configuration on the interface back to default using “default interface” command and apply the interface template along with other supporting commands for IBNS